A blessing for users or hackers?
Despite the ease of use, there are also dangers: not all applications are equally transparent about the access rights obtained. Moreover, users appear to be nonchalant in granting access, so it should come as no surprise that there are more and more reports of affected users. This is also the case with Office 365 customers: on the Internet you can find numerous examples of Outlook users where e-mails were encrypted.
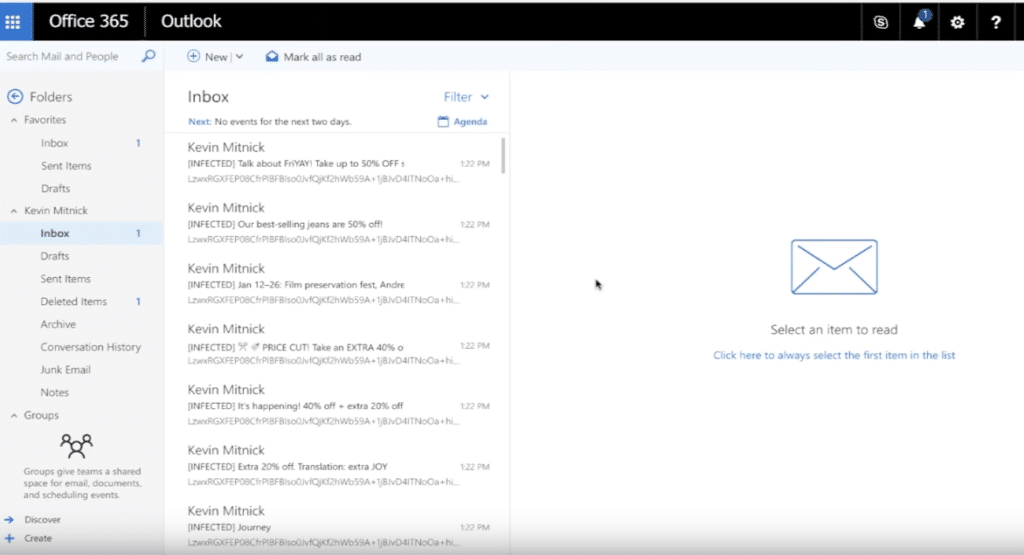
Turn off ‘Application Consent by Users’ our advice!
Hackers have clearly changed the gun from shoulder to shoulder. In order to gain access to our valuable data, they no longer extract login data, but try to connect to malicious applications. For example, with Office 365 users. Our advice? As an administrator in Azure Active Directory, please enable ‘Application Consent by Users‘ off. As a result, end-users can no longer grant new rights to third-party applications. An action that also recommended by Microsoft.
Disabling this option has no effect on existing applications or on the operation of your Office 365 environment.
Is your Office 365 managed by us?
Then you can rest assured: this option has already been pre-emptively deactivated for all our customers. If you, as an admin, still want to enable this function again, we recommend that you first use the ‘Admin Consent Workflow‘ configurable so that new connections can first be approved by an administrator.
If you have any questions about this message, don't hesitate to contact us in time. contactable.