VanRoey » Infrastructure » Microsoft Intune & ScappMan
Microsoft Intune & ScappMan
Manage Third-Party Apps and updates remotely
57% of all hacks could have been prevented by simply installing updates.
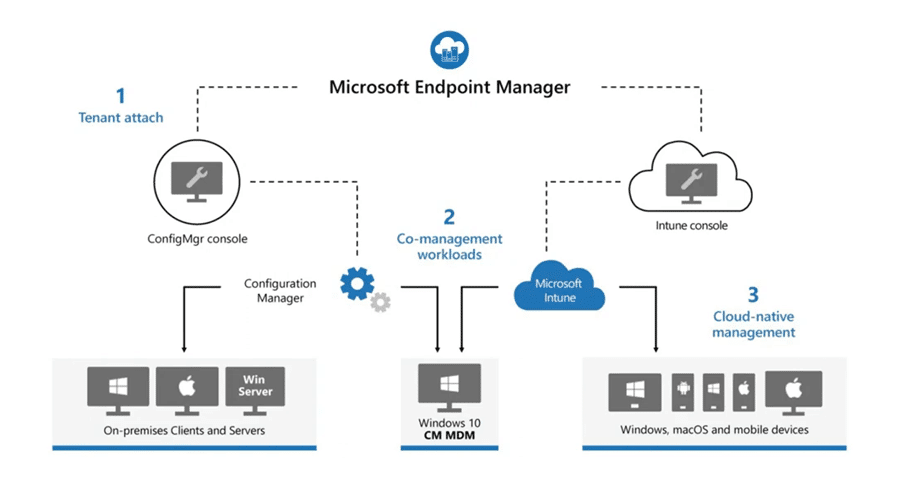
Managing devices, policies, apps & updates is challenging, time-consuming but oh-so-important. Microsoft EndPoint Manager gets you very far, but there are limitations. Belgian Scappman is a cloud service that connects to Microsoft Intune and further extends its capabilities by including:
Automate time-consuming operations such as packing updates
Create user groups in which apps are rolled out
Updates to be rolled out in phases via fast or slow rings
Identify, replace or update shadow IT
Do you already have a Microsoft 365 Business Premium or E3 licence? Then you already have Endpoint Manager!
Will you choose MDM or MAM?Balance between ease of use & safety
Are employees allowed to bring their own devices (BYOD)? Or are both laptops and smartphones 100% kept within management? To protect corporate data, you will have to choose between MDM or MAM anyway:
Mobile Device Management
MDM: full control over devices
-
Push Apps, settings, certificates...
-
Delete the entire device in case of theft
-
Set restrictions (e.g. no games)
-
Full control of device & OS
-
Force security measures such as PIN or biometrics
Mobile application management
Only control over specific apps
-
Company apps like Outlook can be managed
-
Enforce PINs on company apps
-
Limit exporting/saving files
-
You cannot push certificates, settings or apps
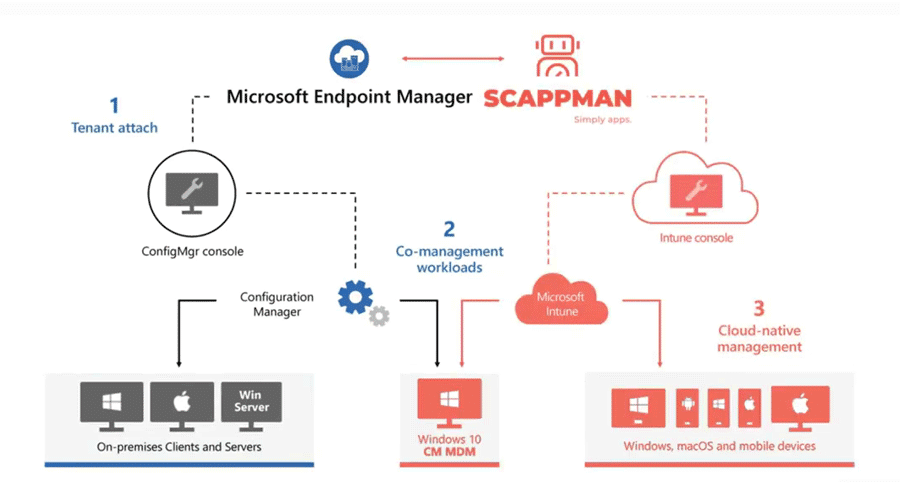
Scappman simplifies & automates both installations and updates of applications via Microsoft InTune
Usually, pushing (updates of) apps via MDM takes a lot of time: downloading, extensive testing, ensuring security, packaging, digital signing... Scappman simplifies this process.
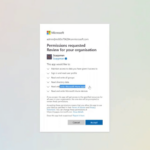
It works through your Azure AD account. After you give it one-time permissions on InTune to manage your tenant with, you can get started. So it is not an additional application that needs to run on all your devices.
Where does ScappMan complement Microsoft InTune?
Auto-Packaging
Scappman scans app vendor websites for updates and automatically 'packages' them. After an extensive test cycle, these are also pushed to your Intune environment.*
Update Rings
You don't always want everyone to get the same update immediately. By putting users in Fast (now) and Slow Rings (e.g. 10 days), you can test thoroughly and intervene in time before rolling out a full release. **
Auto-update
With Intune, you can build a Company App Portal. But installed apps are otherwise not automatically updated. With Scappman, these apps too are automatically updated with the latest versions.
First a notification
When Intune updates apps, it will close the application without notice, which can be a very annoying experience for users ... With Scappman, it first asks whether or not to install now or later.
Push to groups
Not everyone needs to have certain applications. With Scappman, you can define groups, sparing other users from bloatware.
Dependencies
Some applications only work if, for example, a specific .net or Visual C++ version is also installed. This can be provided via Scappman
Installation scripts
Check out the scripts Scappman uses to run installations in the background. You can also modify these scripts to change specific parameters or make targeted changes.
Shadow-IT
If colleagues are free to install software, you at least want these applications to stay up to date as well. Scappman can provide that too.
Reporting
With clear dashboards and useful reports, you track which installations went well, but more importantly: where things possibly went wrong and why. in Intune, that's a really complex process + long waits to receive those log files.
Scappman can do much more and gives numerous configuration options.
View for sure our webinar to see how comprehensive & simple it works.
* Public third-party apps will be packaged by Scappman completely free of charge. But also (updates for) your own apps can be packaged for you -as a service- by Scappman so you can save time and work. ** Of course, in case of zero-days or serious vulnerabilities, you can push a release globally right away.
Find out more about InTune and/or ScappMan
We use this solution with great satisfaction both within VanRoey and with many customers. So feel free to talk to us to count on our experience and expertise.
vat no.*
- Webinar