VanRoey » Managed Services » Security Awareness
Security Awareness
Prevent Phishing Attacks & Risk Behavior of Colleagues
Belgian companies pay up to €100 million (!) in ransom to hackers. In 9 out of 10 companies, phishing is the result of human inattention. Time to make your staff aware of this!
With the platform of KnowBe4 or Phished:
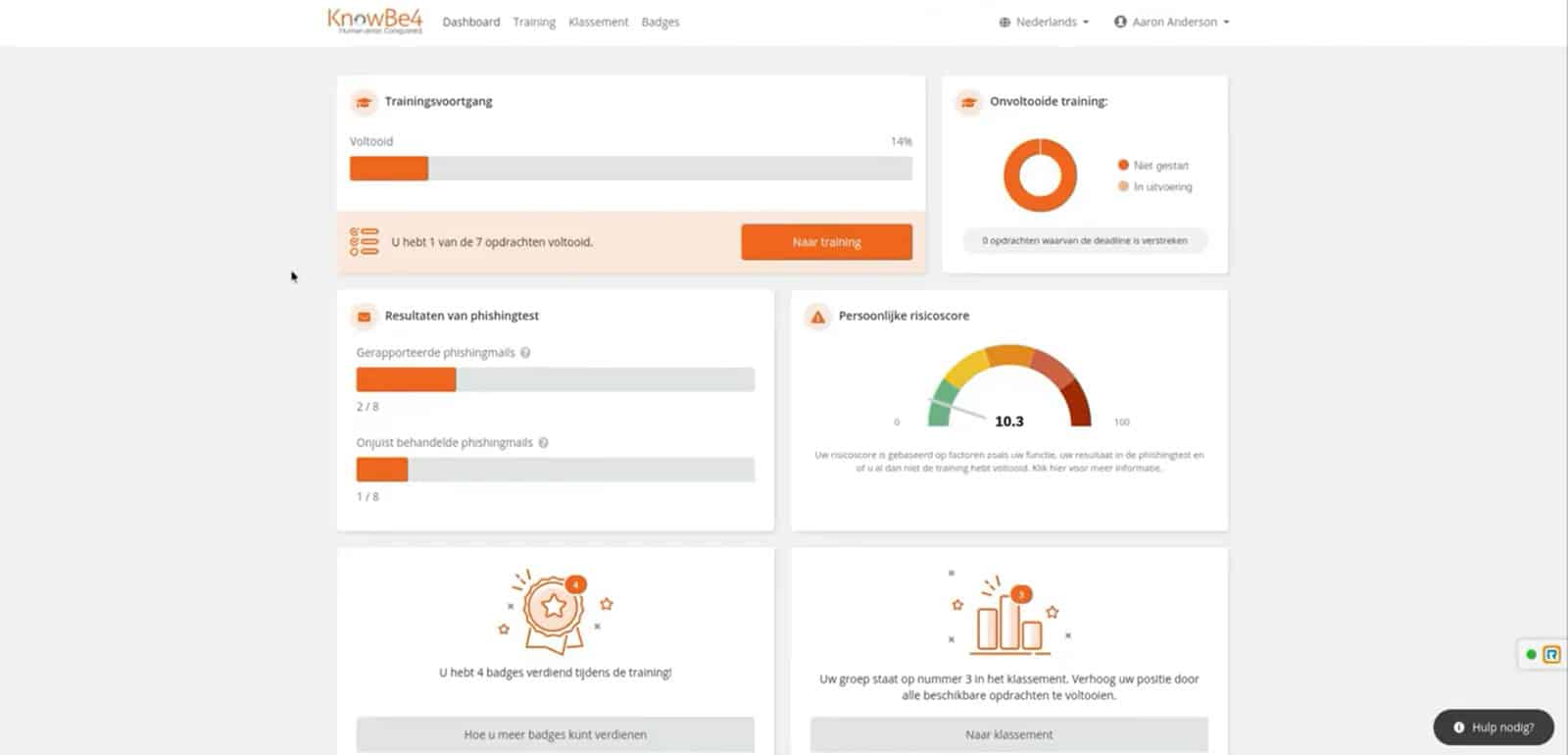
Have clear cybersecurity training in multiple languages and pathways
Send phishing emails yourself, see who gets caught, so the problem can be addressed immediately
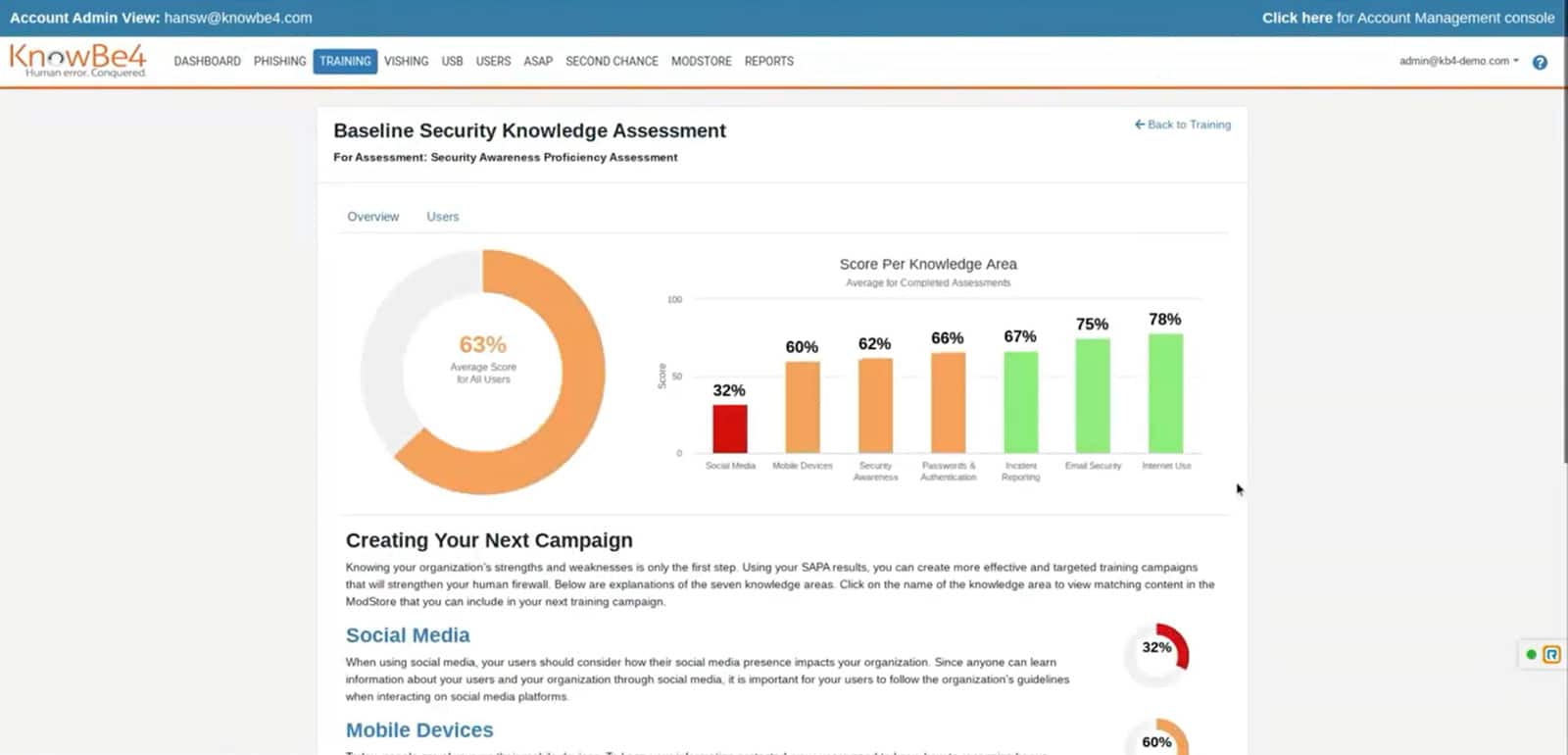
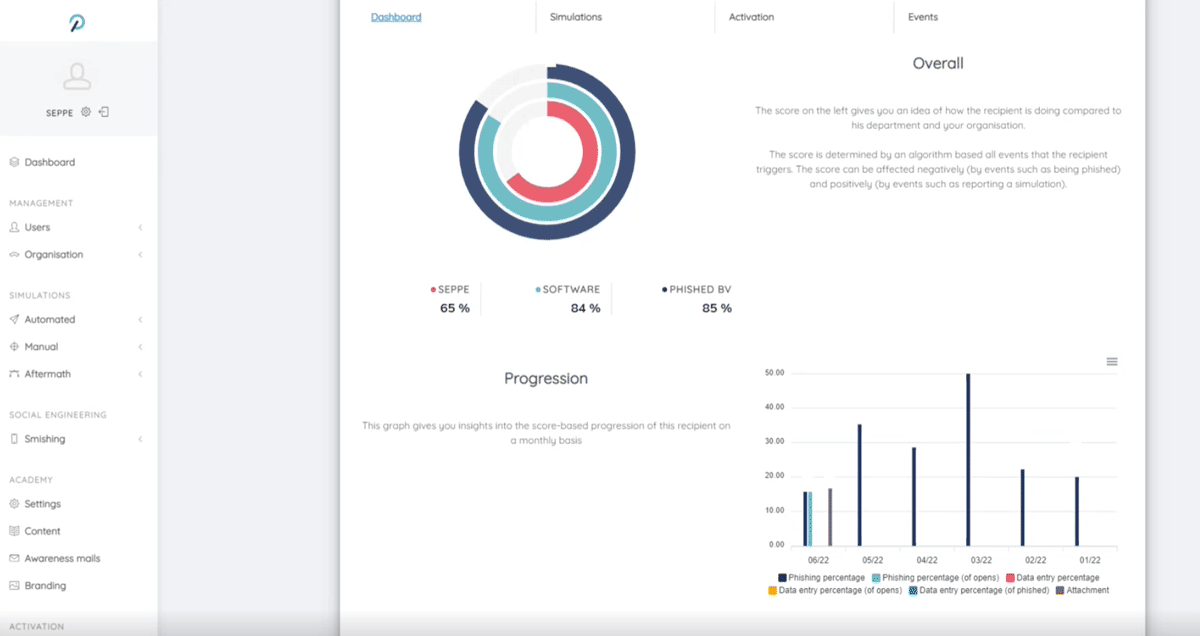
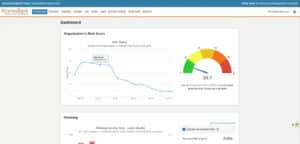
Discover your risk profile as a company, per department or user
You make your organization resilient to phishing, cryptolockers, data loss...
How can you prevent phishing?
With Security Awareness
You invest in firewalls, antivirus and advanced security infrastructure...but often become people forget in the protection model. Yet 40% of your employees tend to click on phishing emails!
After barely 3 months use of a security awareness platform such as KnowBe4 or Phished this quantity decreases by 50%. After one year you are already up to -90 to 95%! This is how you prevent errors that could lead to serious hacks or data loss.
The world's largest player in the field of Security Awareness and absolute market leader (Gartner, The Forrester Wave), ideal for large players
Belgian player that distinguishes itself by simplicity, smart algorithms & local storage (GDPR). Phished has ISO 27001 certification and is SOC2 compliant.
1. Awareness Assessment & Risk Profile
2. Testing and training colleagues
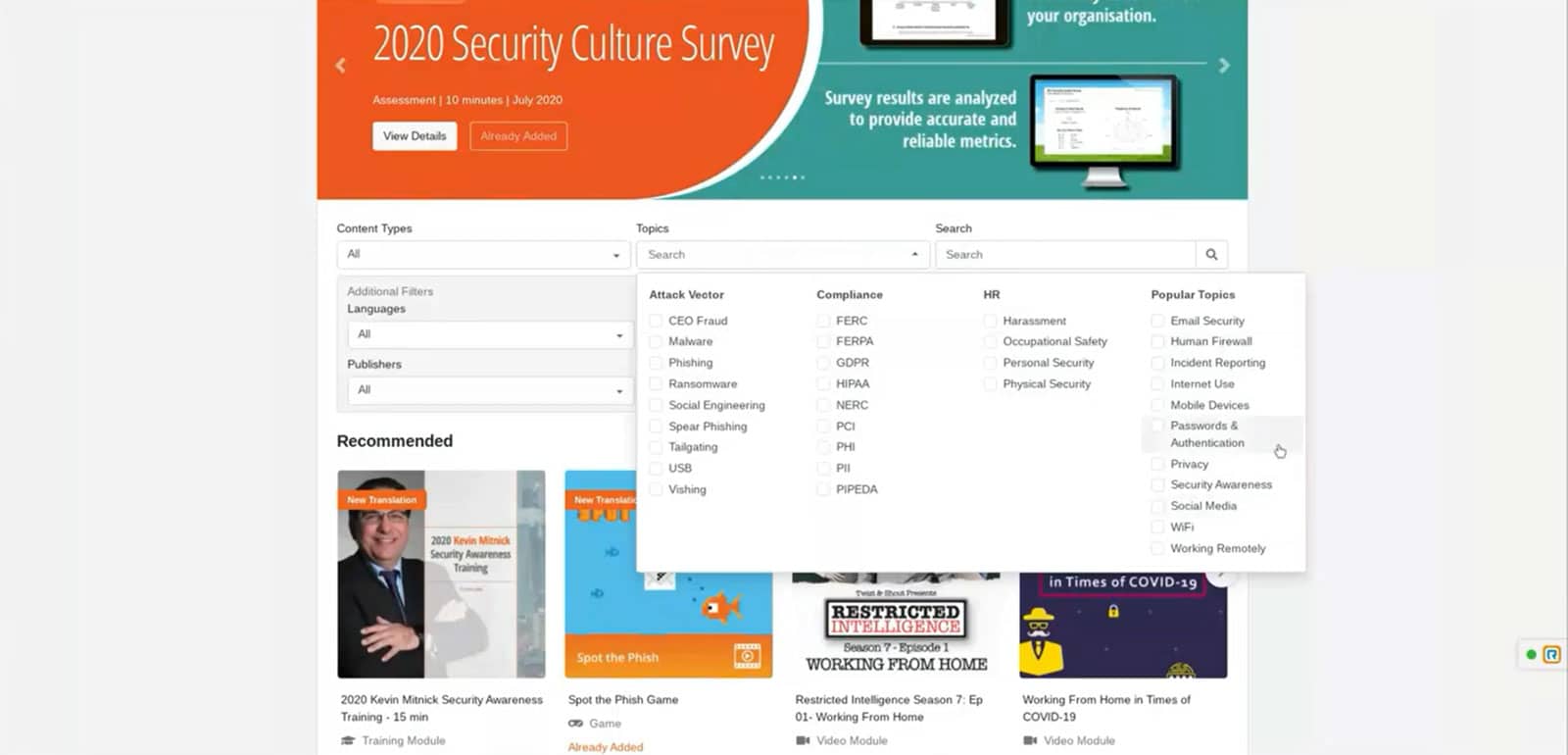
KnowBe4 offers over 1,500 training courses amidst different languages; from Hollywood productions to bite-sized animations. Follow closely who has already followed which routes and put them to the test by phishing tests carry out false phishing attacks:
- Send fake phishing emails to colleagues. Their click is registered and they get to see where they went wrong
- Distributed USB sticks with special software to see who just puts them in their PCs
- With "Vishing" Scenarios (Voice Phishing) test how easy it is to expose colleagues' personal data on the phone
- You can also "Smishing" Work out scenarios in which people are fooled via SMS
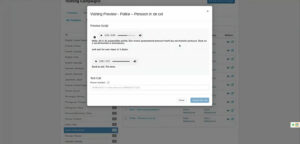
Managed system, simple admin portal
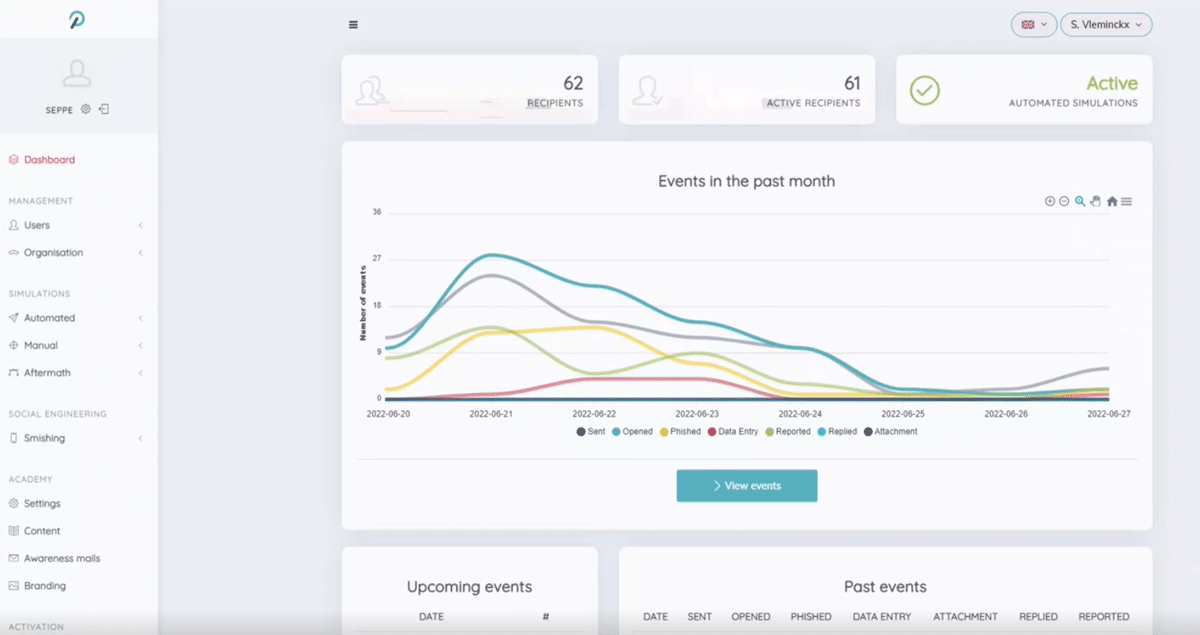
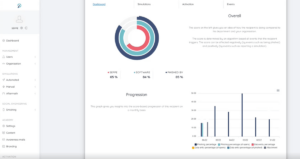
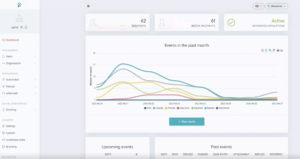
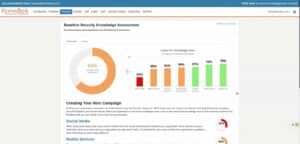
As an administrator you get a comprehensive portal with numerous configuration options, rich insights into training progress and evolving risk scores.
- Users can be linked to the Active directory
- Classify users according to their role, language, location, level...
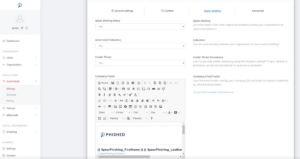
- Create training and phishing campaigns, use prepared USB stick software... Choose from numerous templates (difficulty levels...) or personalise messages as you wish
- Once set up, the (continuous) training process is largely automated. Colleagues who score badly are mapped out and shot trained/tested until the risk score is reduced to a minimum
The extensive reporting tools make the platform ideally suited to ISO standards to pay. In addition, you can also Upload your own videos or training sessionsPour it into a campaign, assign scores to it and provide reporting!
What is the ROI of the KnowBe4 platform?
A study From Forrester shows that:
- You ROI on a three-year deal is 276%
- You payback time lies on three months!
- The number of clickers on phishing emails decreases from 19.2% to 2.8%.

More info, a conversation or free trial account?
vat no.*
- Webinar
How does Phishing work?
1. An attacker poses as someone known and misleads you by e-mail, phone or SMS. The intention is that you answer his question or open his forged link.
2. When you visit the forged website, either malware is downloaded automatically or an attempt is made to extract sensitive log-in data.
When you go into phishing, a hacker takes over your system or account in less than 2 minutes on average.
*Source: KnowBe4
What types of phishing are there?
By means of impersonation an e-mail tries to impersonate a well-known brand or service in order to retrieve your log-in data.
Victims are made to think that, for example, sexually tinged webcam images of him or her have been recorded or that you know your secrets such as 'adultery' or fraud. In exchange for payment(s), they do not publish it.
Infected attachments are usually quickly filtered out. In this case you will be offered an infected download link. The file may look perfectly normal, even if it has been opened, but in the meantime you are infected.
These mails (or telephones) seem to come from important colleagues, partners or customers, aimed at decision-makers or bookkeepers hoping to execute a payment order.
10 tips to prevent phishing
You want to avoid cryptolockers, malware and data theft. Protecting both network and devices is a start and an absolute must, but there are many pitfalls that end users need to recognize and avoid, because one click can render the entire organization technically unemployed and might put sensitive data in jeopardy.
-
Public information
Social engineering and Spear Phishing means that people collect as much personal information about you as possible in order to make a targeted strike. So be careful with public profiles on Facebook, Linkedin, Twitter... If, for example, you know your license plate, garage and car type, then you can send false maintenance invoices to your accounts.
-
2 Factor Authentication
More and more platforms offer the option to sign up using your password + a unique code that is only shown on your smartphone (via SMS or an app). Even if scammers have your username and password, they are still powerless because they don't have your smartphone.
-
Senders
If you have any doubts about the sender, you can open a mail in Outlook and check the properties of the mail under 'file'. The mail headers contain some technical information, but there is a lot to deduce from this in terms of legitimacy.
-
URLs
When you move your mouse over links in an e-mail, you will see the url to which it leads. Fortis.be becomes fortis.bank.ru. This way, you will soon recognize that you are being redirected to an unofficial site.
-
By phone
NEVER go through an application process over the phone together and never release personal data unless you know the person on the other side of the line and trust them completely. With the right background information, scammers can convince even the least gullible people...
-
Attachments
With unknown senders who send you a PDF, Xlsx, Docx, exe... or .zip, you always run the risk of getting a cryptolocker or other malware. We solve this with sandboxing, in which the mail is first fully sifted through in a virtual environment and all links are checked.
-
Extraordinary
Does your ICT department suddenly ask you to 're-register' or 'verify data' on a page? Or does an unusual question from HR push itself with a zipped attachment about your salary? There is a good chance that it's a deception. It never hurts to verify whether it's real by telephone. - Spam filterA lot of non-personalized phishing is sent in bulk and soon appears on the blacklists of well-known anti-spam filters. It's an obvious one, but a professional anti-spam is a must.
-
Suspicion
Your business manager e-mails to make a large transfer 'urgently and discreetly'? Call him or her first about it. Or your supplier sends an invoice by e-mail or post with a 'change of account number'? Again, one phone call can limit a great deal of damage. -
Passwords
Use unique passwords and change them regularly. You really don't want to be responsible for phishing mails sent from your account to your network because you use the same password on e.g. Steam or iTunes.