1. Start your network with a good design
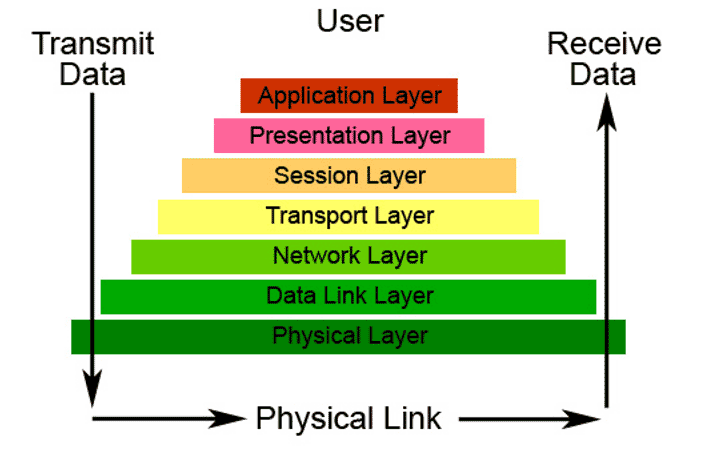
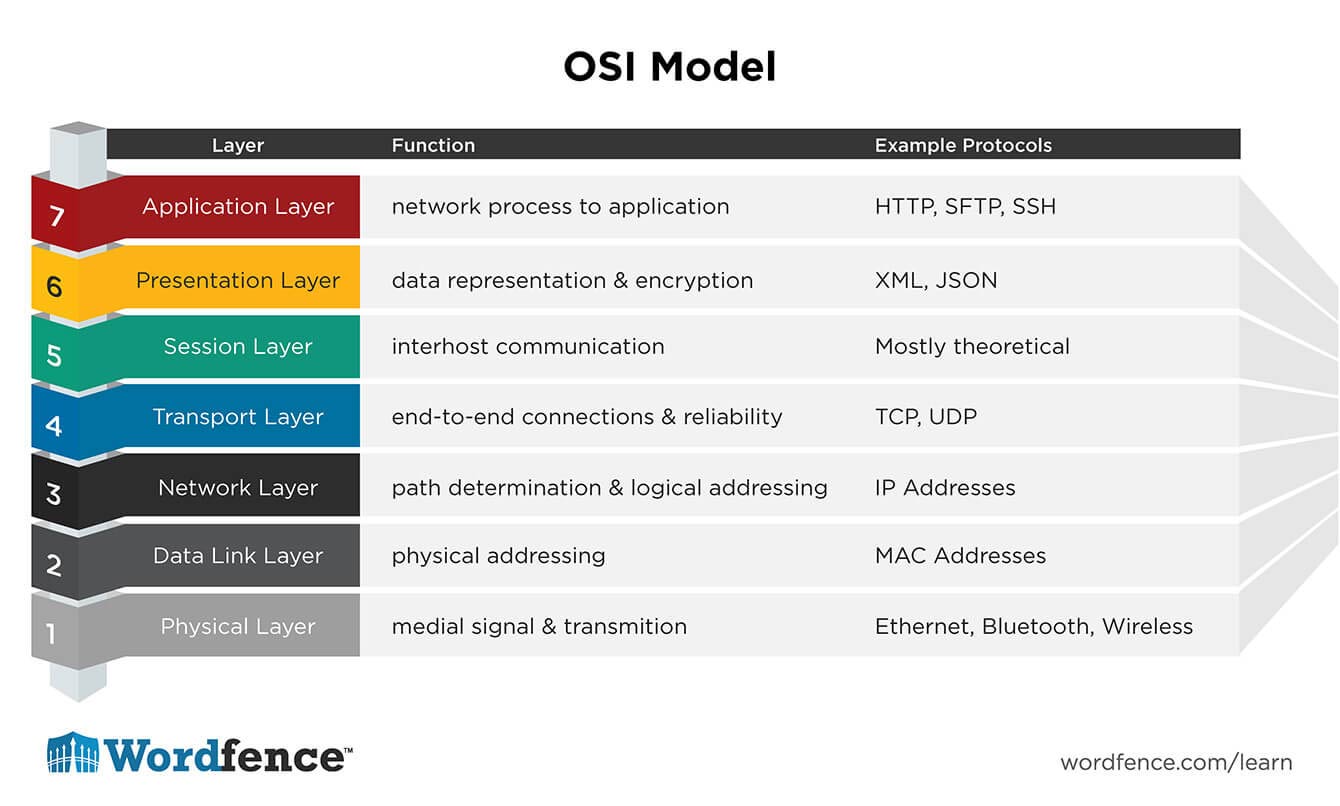
In order to build a good design, we start from the basics, based on the OSI model.
We always start at layer 1 and look at the cabling between the patch cabinets. I notice that sometimes a fiber optic connection is made between the patch cabinets with the reasoning: "This way they have more bandwidth on the network".
To frame this, I regularly use the comparison between 1 kilo of plumes and 1 kilo of lead; 1 gbps over glass fibre or 1 gbps on copper remains 1 gbps, regardless of the medium used. Only when patch cabinets are more than 100m apart, glass fibre should always be used.
Fiberglass
If there is a demand to increase the speed to 10Gbps, we can in some cases re-use the fiberglass, but within 100m we can easily use cat6a copper cabling.
The table below provides an overview of the distances for fibre optic cables to copper as well as the types of fibre optic cables.
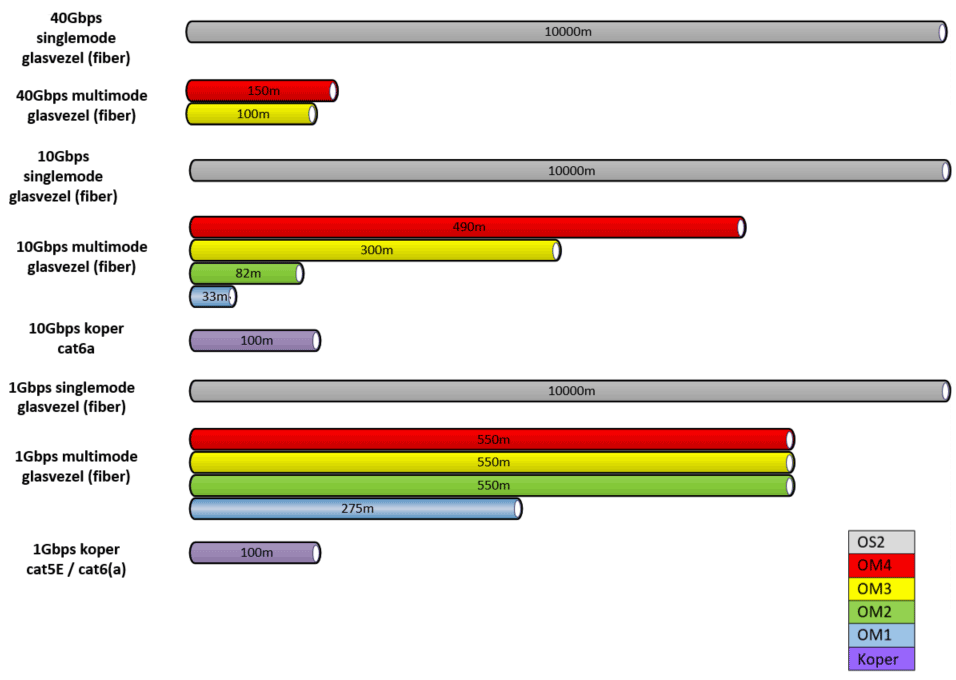
In addition to longer distances, fibreglass can also bridge another obstacle; If copper cabling runs along electromagnetic fields, such as high-voltage cables, this will result in a loss. Fiberglass is not affected.
There is a drawback to these advantages of fibre-optics: the cost price, not so much the cost of laying and connecting the fibre-optic cables, but rather the cost of the actual connection of fibre-optic cables to the switch. We have to put 'gbic's' or 'transceivers' in the switch in order to connect the fibre-optic cables, and it is these gbic's or transceivers who are pushing up the cost price of fibre-optic cables.

2. Performance ≠ bandwidth
After layer 1 we arrive at layer 2 of the network. Now that we know the cabling, we can investigate which switches are present in the network. We talk about layer 2 or layer 3 switches, these layers are a reference to the layers of the OSI model. Where the cabling itself is layer 1, the switches are located in layers 2 and 3, respectively in the data link layer and the network layer.
In practice, we notice a lot of misconceptions about switching. On the one hand, end users think that a gigabit switch is sufficient for their network. On the other hand, consumer products and business equipment are often aligned, because both devices promise gigabit network speeds. But on the other hand, there is a world of difference.
For example, servers use 2 processors with 8 to 10 cores per processor, 128GB of RAM and preferably SSD disks to provide sufficient IOPS.
Unfortunately, these servers are then connected to entry-level or consumer-based switches, which reduces the performance of the network. It is important to know that a switch also has a processor and RAM memory on board to process information as quickly as possible.
To make the obligatory comparison with a car; you can leave on holiday with a 2 HP as if a sports car and you will normally reach your destination with both devices, but with the sports car you will be much faster. The "engine" of a consumer switch compared to a business-grade switch is much weaker, especially as the basis of your network, we always recommend sufficiently high-performance switches so that there is as little "latency" (or delay) as possible, as we have been able to demonstrate this to a number of our customers in a demonstration, and we will replace a core switch with a core switch.
3. Is stacking necessary in your network?
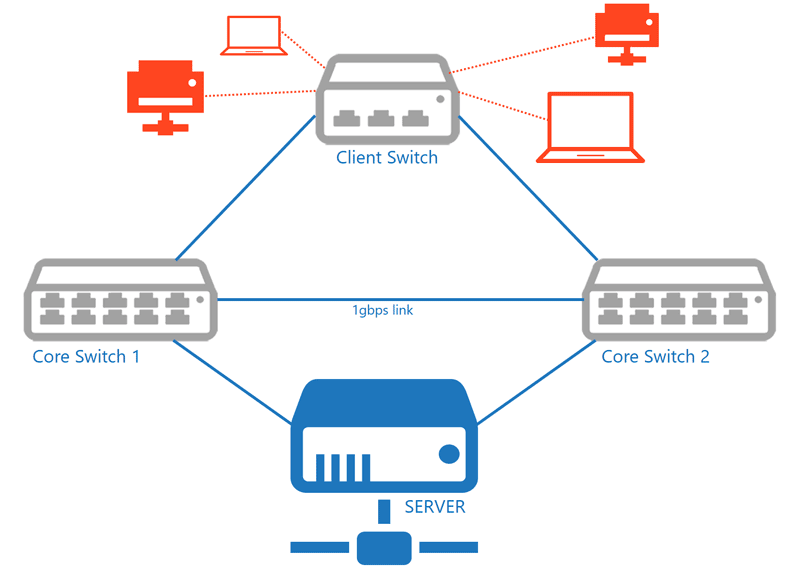
How do the logical connections between the patch cabinets work and how is everything connected? We look at the topology of a network.
The easiest way to build up redundancy is to connect a 'Client switch' for the PC's with 2 cables. Two physical cables to 2 separate core switches in the server room. In this case we have redundancy, but failure of a core switch is accompanied by temporary network failure and server connectivity.
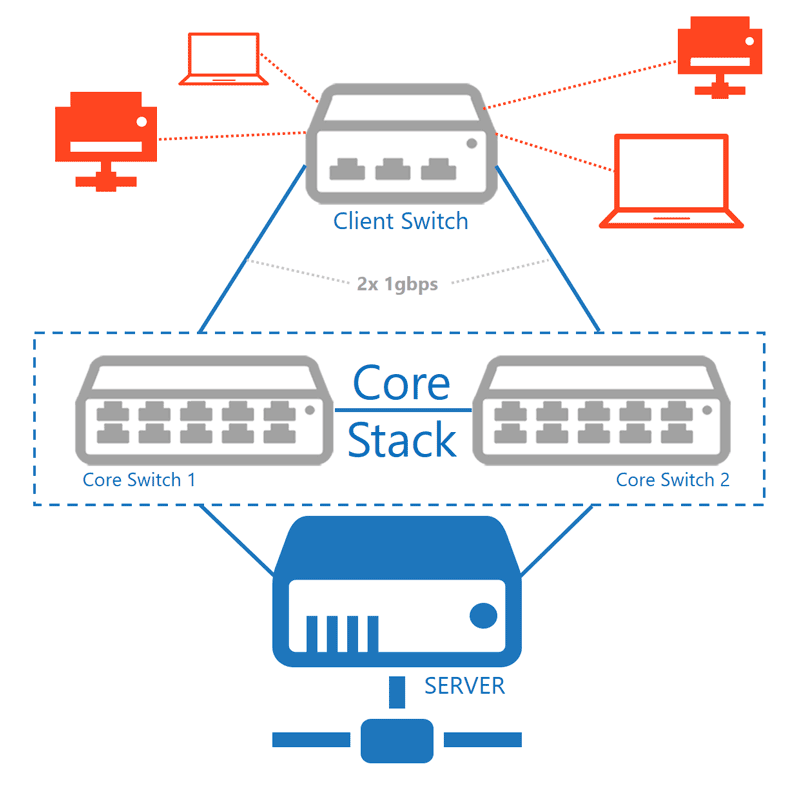
This is why in many cases we use 'stacking' within the network. By bundling 2 physical core switches, they present themselves on the network as 1 device. This has two major advantages: On the one hand, the 2 links can be used actively at the same time, resulting in a doubling of the speed (2Gbps); on the other hand, end users do not notice any loss of server connection in the event of a failure of a core switch.
A small intervention on the core switching can therefore ensure continuity and realise an additional increase in the bandwidth.
4. Security and the Internet of Things
Today, all equipment is expected to be connected, from traditional equipment (PCs, printers, access points, IP cameras...) to new things like solar panels, air conditioners or other home automation. Everything depends on the company network and we assume that we can read the data anywhere in the world - via the cloud or an app.
Professional networks, both wireless and wired, are extremely tightly shielded to prevent hackers. But when communication with equipment such as solar panels or home automation is opened to read them remotely, there are major risks.
Think for example of the website insecam.org where everyone can view numerous unsecured IP cameras all over the world. Living rooms and office environments are open and exposed on the internet.

Data theft intrusions on the network are nowadays largely done from the network itself instead of from the internet. It often happens that a mini-PC, e.g. a Raspberry Pi of less than 100€, serves as a physical backdoor to break into the network. If you connect this mini-computer to the network with a network cable, the built-in 4G connection can be used to provide remote access to the hacker.
Such issues can and should be avoided. Proper segmentation of your network combined with the use of Network Access Control (NAC) over the wired and wireless network. We prefer to identify each device connected to the network. Then we can apply the necessary policies. With a well-built firewall configuration, the necessary traffic to and from the Internet can be controlled and contained.
For such configurations, the network team and security team at VanRoey.be work very closely with you, the customer, to ensure that your environment operates optimally and securely.
share this post: