VanRoey » CyberSecurity » Zero Trust
Zero Trust
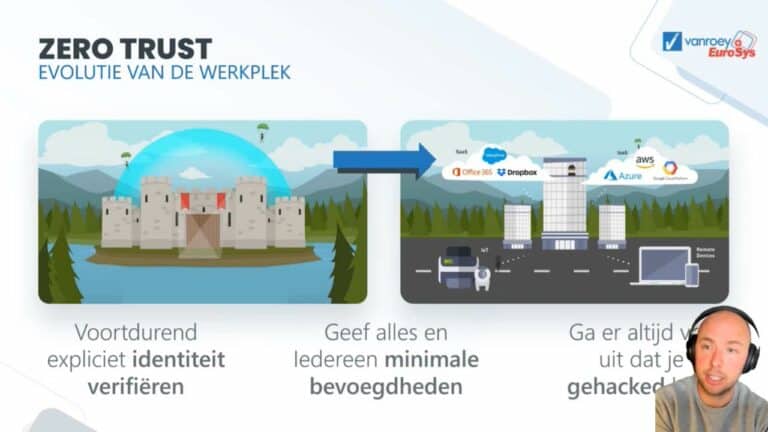
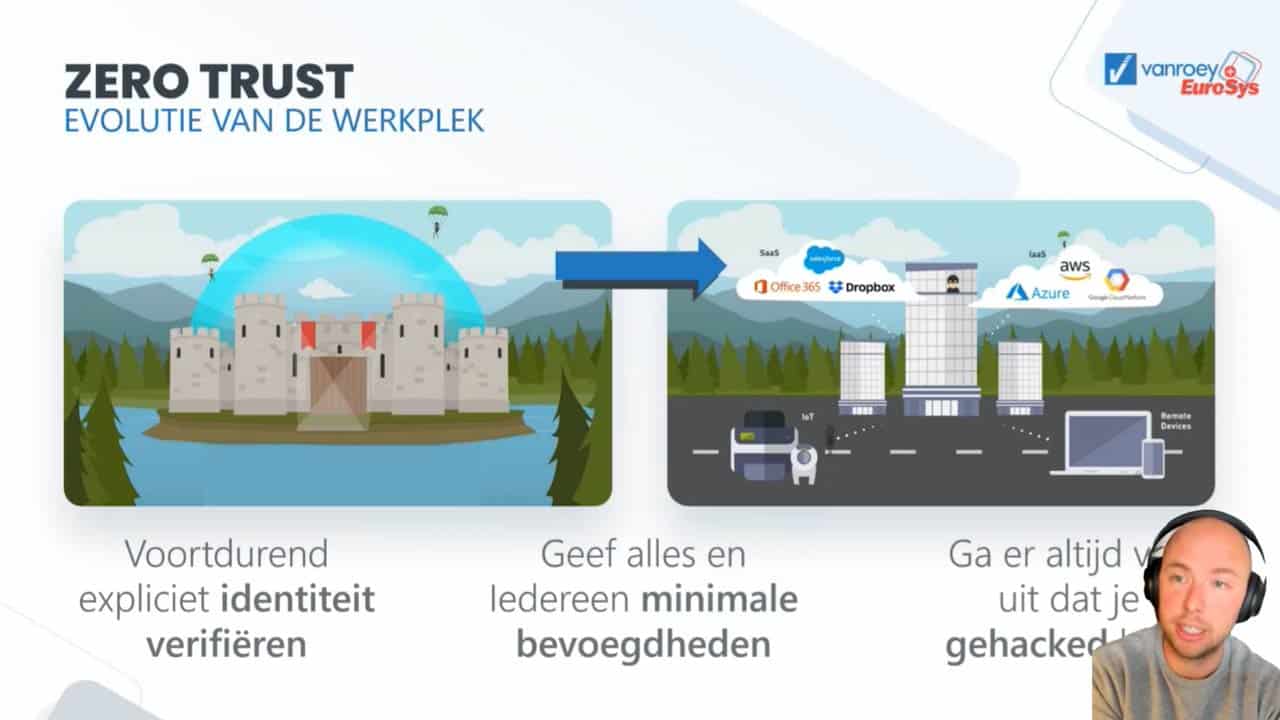
Healthy distrust ensures safe environment
Organisations are no longer limited to one clearly protected digital environment. And not just any user should be allowed to see everything. Zero Trust is a security strategy that:
Verifies who the user is at all times, even in trusted environments
Granting rights explicitly instead of taking them away
Dividing your network into 'Implied Trust Zones'
Default users and devices blacklist
3 Core principles
Zero Trust is designed to adapt to the complexity of the modern environment. It protects corporate data wherever it resides.
Explicit verification
Always and thoroughly verify & authorise when an end user/service requests access to a certain service or company data. In both cloud and internal environments.
No access as a basis
Access rights are kept to the bare minimum with solutions such as 'just-in-time' and 'just-enough' access... If an end user is compromised, the damage remains limited.
Always assume malpractice
we will assume that the environment is compromised or that a cyber attack will happen. As a result, we will create an active, defensive strategy that ensures we are always prepared.
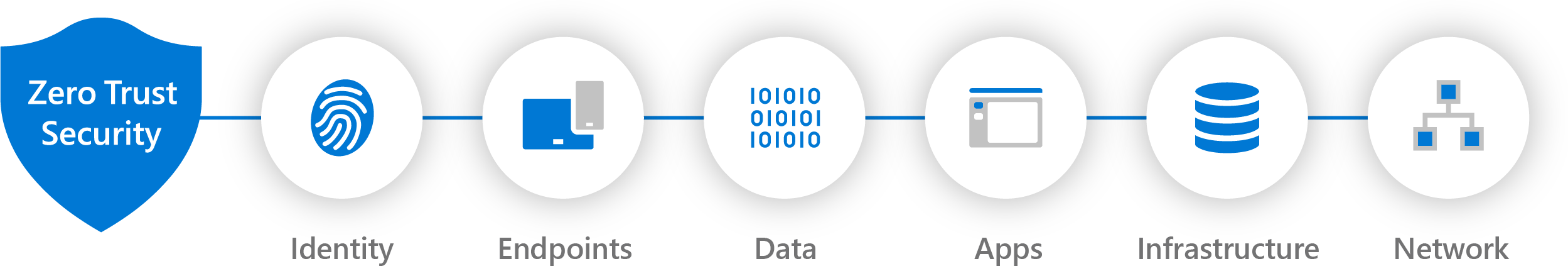
Securing
Id.
Regardless of whether they represent persons, services or devices; When an identity tries to gain access, we will check and verify it.
To this end, we use solutions such as password policies, conditional access, multi-factor authentication, the principle of 'minimum authority'... This is called Identity Management & Access Control.
Securing
Devices
All devices on which end users work are configured securely. We distinguish between organisational and personal devices.
This includes securely configuring laptops, keeping applications & firmware up to date, providing antivirus & EDR, enforcing policies,... This is where we speak of Endpoint Management.
Securing
Data & Apps
Of course, we also ensure that data is safe, even when it leaves the secure business environment.
Confidential data is classified & encrypted as such. Access can be restricted based on these attributes. We will also secure external applications (e.g. Salesforce) with conditional access.
Securing
Infrastructure
We build a Zero Trust architecture. Think about implementing telemetry to detect attacks, but also to services such as (among others) network access control (NAC) and firewall configurations to restrict access to the network.
So it goes beyond just configurations within your cloud environments as Microsoft 365.
Implied Trust zones
The zero trust principle is based on segmentation. It creates several clearly delineated secure networks that we call implied trust zones. Each with their own Authentication & authorisation methods and active monitoring.
Zero trust is not something you achieve overnight. It is a mindset and a complex process that requires constant adjustment. It is important to think this through fundamentally.
We provide you with a pathway to evaluate the functionality, user experience and deployment of these different features within Microsoft 365, among others, to prevent, detect and respond to cyber attacks and protect intellectual property.
This through a concrete roadmap who have the necessary Will map budgets & resources to migrate to a modern environment based on Zero Trust.
Trust must be earned
Give the chance to our people, with years of experience in thousands of diverse environments, to apply their knowledge to your environment and gain your trust.
vat no.*
Why VanRoey.be?
- We are ASDP Partner at Microsoft...this guarantees that within 15 minutes, we'll have a Level 3 Specialist for Azure, Office 365, Dynamics 365... ...with access to their data centers.
- VanRoey.be has +25 years of experience in thousands of different environmentsThat knowledge comes in handy.
- Thanks to our maximum partnerships With companies like Microsoft, HPE, Veeam, Fortinet... we can force manufacturer support if necessary.
- We have lots of proven case studies.
- We're a company with focus. That leads to maximum certification and partnerships, and even (EMEA) awards..
- The fact that the Belgian government has recently security contract with us again extended by 4 years speaks volumes.
- Recording