VanRoey » CyberSecurity » Security Strategy
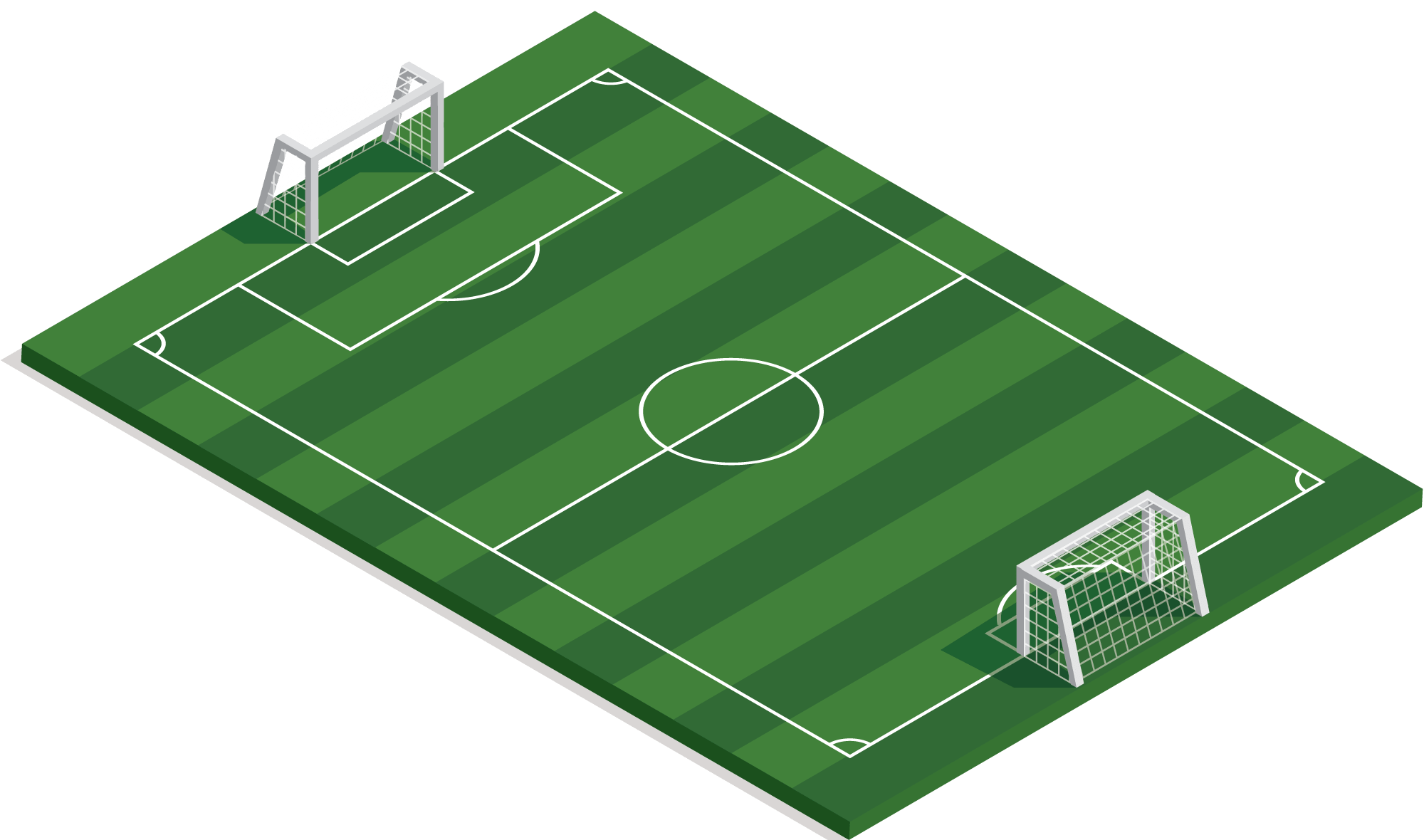
Security Strategy
Discover the strategy that suits you best
"Often something has to happen before something happens.”
-Johan Cruijff
Hackers and malware use a variety of tactics to attack your organisation. How do you protect yourself against these? Choosing the right solution is complex and waiting is not an option.
Winning is not possible
This enemy will never stop attacking. It's Cruijff again who said: "If you can't win, you have to make sure you don't lose." Because one hack or virus can be disastrous.
A solid team is needed
One star player means little without teammates. This also applies to security solutions. The right team, backed up by the right strategy, determines whether you can master the situation.
We like to present our solutions as team players that we can use tactically:


Goalkeeper
More info Essential basics: Antivirus + Antispam + Firewall + Backup & Patch Management
SECURITY AWARENESS
What's this? Visit page
Multifactor Authentication
What's this? Visit page
Password Policy
What's this?
Encryption
What's this?
Printing Security
What's this? Visit page
Client Security
What's this? Visit page
Mobile Device Management
What's this? Visit page

Network Access Control
What's this? Visit page
Wifi security
What's this? Visit page
Reverse Proxy
What's this?

User Entity Behhavior analytics
What's this? Visit page

Cloud Access Security Broker
What's this?

Managed ICT Services
What's this? Visit page

Coach VanRoey.be
Why us?
VanRoey.be has over 25 years of experience in thousands of different environments and numerous certificates. This knowledge is very useful to put together the perfect security set-up.
#1 KEEPER
A collection of essential interventions: antivirus, antispam, sandboxing, patch management, backup and firewall. If anything should come through,
- the good antivirus and antispam will stop most of the attacks;
- a firewall will keep out malicious links, sites and hidden connections;
- sandboxing will extensively test unknown downloads or attachments for misconduct;
- Patch management will keep firmware and software up to date as much as possible in order to close known leaks;
- a good backup - in case of an emergency - will save your organization.
#2 MANAGED SECURITY AWARENESS
A managed Security Awareness Training determines which employees are susceptible to false emails or websites that try to steal data. We regularly test them with traps and alert them to their mistakes and the possible risks.
#3 MULTI FACTOR AUTHENTICATION
Getting a strong password from a user is easier than expected. Therefore, in addition to the password, we ask you to enter a unique time-based code that will be texted to the user.
#4 PASSWORD POLICY
Do your employees use powerful, unique passwords or do they always use the same, weak password? A good policy can require, generate, securely pass on and manage complex passwords using tools.
#5 ENCRYPTION
A stolen laptop or smartphone contains a wealth of information. To prevent thieves from accessing this information, the encryption of this data is of the utmost importance.
#6 PRINTING SECURITY
Just like PCs, printers have network access, memory, a hard drive and a processor, so why put them in your network in an unsecured way? Protect the BIOS to ensure integrity so that no one can read the prints. Even unguarded documents that are left unattended pose a major security risk.
#7 CLIENT SECURITY
Enhance security on devices with fingerprint readers, smartcard readers or a privacy guard. But it goes beyond this... Advanced malware nestles outside the OS or storage and infects the BIOS or RAM memory. HP Sure Start and Sure Run guarantee the integrity of BIOS and software and the systems are self-healing, so there is no question of failure.
#8 MOBILE DEVICE MANAGEMENT
With Mobile Device Management, you enforce (security) policies on employees' mobile devices (iOS, Windows and Android). It requires them to configure a lockscreen, set some applications as default, lock or delete devices, data or apps remotely, etc...
#9 NETWORK ACCESS CONTROL
Make sure that an unknown device does not gain access to your network. Loose network cables or leaked WiFi passwords pose a very high risk of physical hacking. With Network Access Control, only employees' verified devices connect to the company network.
#10 WIFI SECURITY
An encrypted connection with strict WPA-2 or 3 security and always up to date accesspoints is obvious. But how do you deal with guests? With customers in your shop? Hundreds of students in your school who have to stay separated from the network teachers and management... use?
#11 REVERSE PROXY
A reverse proxy has many functions. As far as security is concerned, it can do following things:
- Protects your domain/website by analyzing external access requests first and before they can (partially) reach your environment.
- Prevents DDoS attacks in which millions of access requests simultaneously attack your servers in the hope of penetrating or crippling them.
- Prevents external parties from gaining insight into your internal network.
- Add an extra layer of security to sites that don't provide security by default
- ...
#12 USER ENTITY BEHAVIOR ANALYTICS
Prevents risks by identifying deviant behaviour through artificial intelligence, such as employees who download the customer database and then put it on a USB stick or upload it to their private dropbox. Colleagues who were still working from Antwerp a quarter of an hour ago and are now 'suddenly' logging into the document libraries from Ukraine... With UEBA, you can detect seemingly innocent behaviour that, in combination with a number of factors, is less innocent than it might seem at first sight.
#13 CLOUD ACCESS SECURITY BROKER
A CASB provides a layer of security between your company network, your users and the various cloud applications (such as Sharepoint Online, Salesforce, ...) that you use in your company, giving you the same layer of security inside and outside your company network. Within the company network, you will be able to log in quickly and easily, and in an internet cafe in Shanghai, you will have to endure additional layers of security to prove that it is you. Next to this it can detect sensitive content -such as Visa card numbers- are being shared.
#14 MANAGED SERVICES
By leaving the management of your park in the hands of a small army of certified experts with a clear plan, you will avoid many risks such as shadow-IT and security leaks. Extensive documentation, intelligent monitoring, automated patching... We can guarantee uptime and safe operation, but above all fast action thanks to response times 24/7 within 4h or even 1h. This ensures that your park immediately gets the necessary protection in its most vulnerable moments.
COACH VANROEY.BE
- More than 25 years of experience
- Certified 'Level 3' security experts
- The highest partnerships (Fortinet Platinum + Partner of Excellence, Microsoft Gold Partner, HP Platinum Partner, HPE Gold Partner...)
- Excellent track record
- Numerous satisfied clients such as Torfs, Soudal, Government agencies, Groep Van Roey, Flanders Make, Suez, hospitals, schools...
re-watch webinar
On 14 October, Windows 10 will end. In this webinar, we will take a closer look at the opportunities W11 offers for a better managed and secure environment.
Example setups
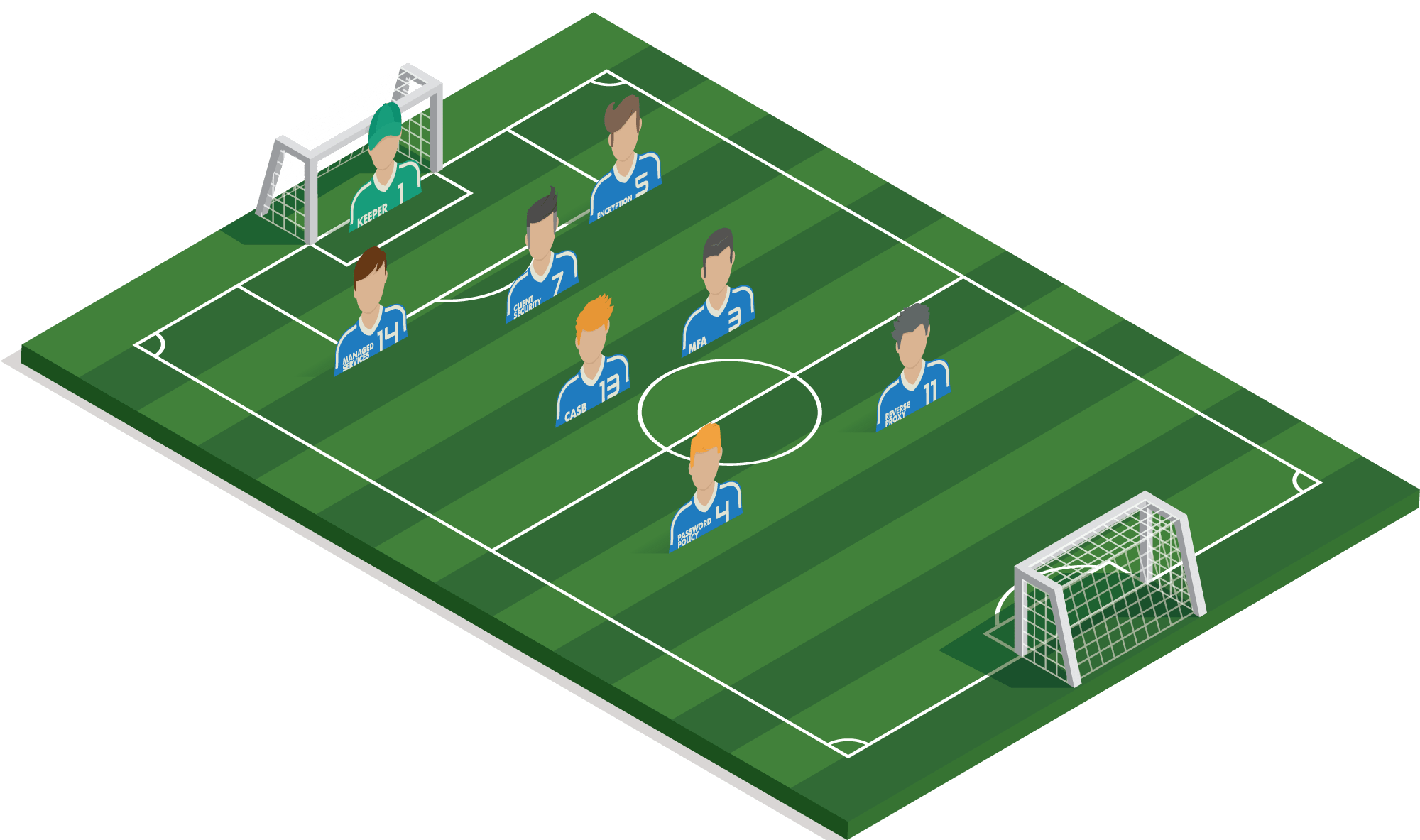
#1 Goalkeeper
A collection of essential interventions: antivirus, antispam, sandboxing, patch management, backup and firewall.
1 of 8#13 CASB
Follows data traffic between the different cloud solutions, detects when, for example, visa card information is shared in an unsecured manner, ...
2 of 8#4 PASSWORD POLICY
Employees who leave service can be quickly ‘excluded’ from applications. One breach will also not ensure that all systems can be hacked at the same time.
#3 MFA
As an extra layer of security for the various cloud applications, an extra code must be entered in order to log in. For example, if a password is lost, there is no immediate risk of an infringement.
4 of 8#5 ENCRYPTION
Disks are encrypted so that no sensitive information falls into the wrong hands in case of loss of devices (e.g. GDPR).
5 of 8#6 REVERSE PROXY
Digital marketing agencies also often offer web hosting and online portals where customers get insights. These need to be well protected.
6 of 8#7 CLIENT SECURITY
The confidential information of customers does not fall into the wrong hands, even in the event of theft or loss.
7 of 8#14 MANAGED SERVICES
Guaranteeing uptimes of customer websites and portals is vital. Small/medium sized agencies need to focus on creativity and services instead of ICT.
8 of 8Example strategy
MARKETING AGENCY
A marketing agency has access to confidential information about the business strategy of their customers: they expect that there is a high level of security on the different mobile devices of the users.
Cloud access is vital since it is mainly mobile and cloud applications such as Adobe Creative Cloud, Office 365, Google Analytics, Active Campaign and many other SaaS tools which are being used. No access to the Internet means no access to the work environment: vital components to the Internet are best duplicated.
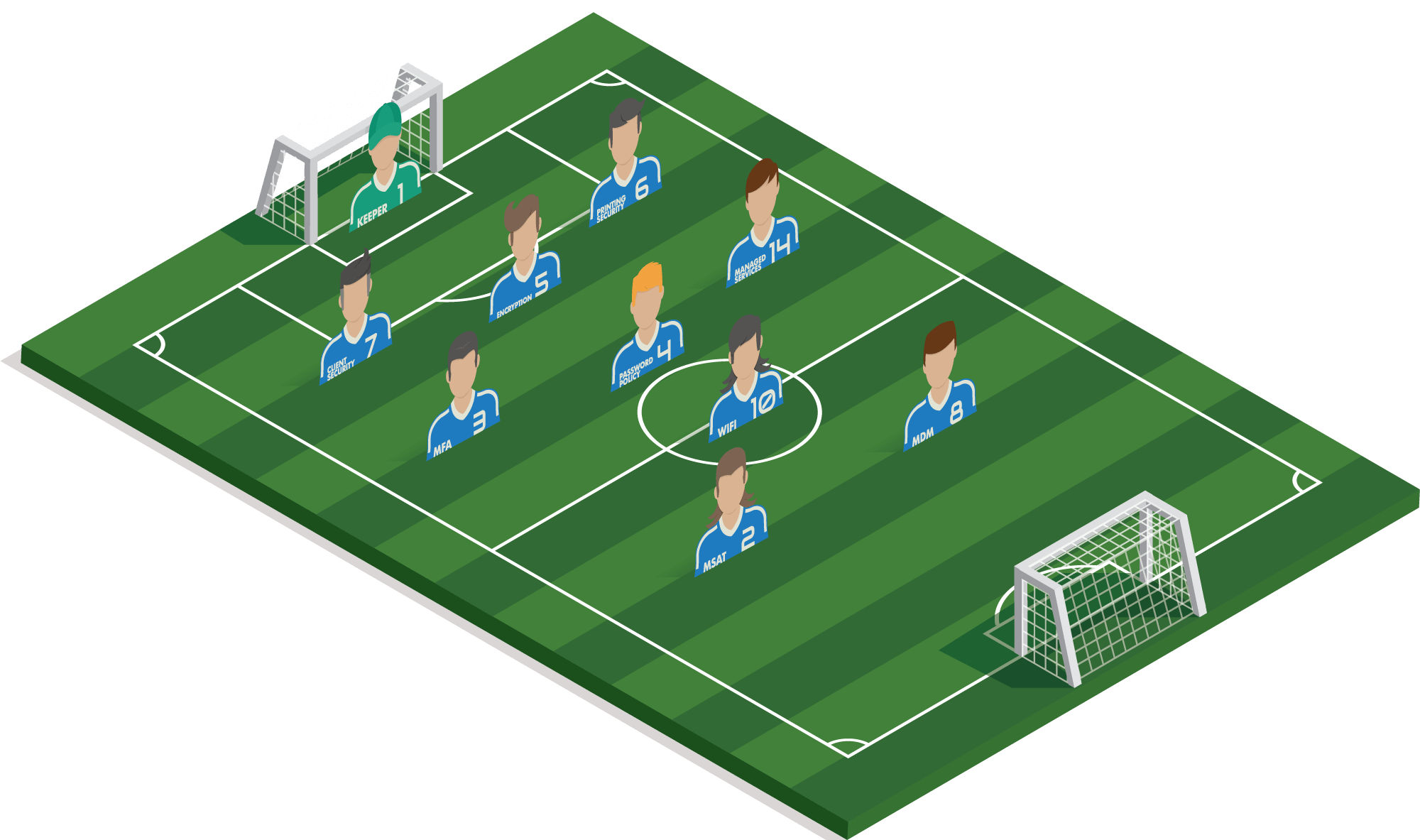
#1 Goalkeeper
A collection of essential interventions: antivirus, antispam, sandboxing, patch management, backup and firewall.
1 of 10#14 MANAGED SERVICES
Keeping infrastructure and software up to date is impossible for our own team of application specialists, which is why they should outsource it.
2 of 10#3 MFA
As an extra layer of security for the various cloud applications, an extra code must be entered in order to log in. For example, if a password is lost, there is no immediate risk of an infringement.
3 of 10#7 CLIENT SECURITY
Ensure the integrity of the software and hardware used and prevent unauthorized access.
4 of 10#4 PASSWORD POLICY
With strong and unique passwords, you can also prevent a single breach from giving access to a large number of accounts.
#5 ENCRYPTION
If a tablet or notebook is lost, the (in)honest finder will never be able to access the available data. Another plus point is GDPR.
6 of 10#8 MOBILE DEVICE MANAGEMENT
Manages all tablets on site: the configuration, application deployment, Wi-Fi settings are automatically rolled out. And in case of loss, they can easily be deleted.
7 of 10#2 MANAGED SECURITY AWARENESS TRAINING
Construction companies are often targeted for ‘CEO fraud’. Staff must be continuously trained and alerted to prevent this type of fraud.
8 of 10#6 PRINTING SECURITY
Prevents single invoices, contracts or blueprints on devices and ensures that no one can read the print instructions
9 of 10#10 WIFI SECURITY
Avoid SSID Spoofing or wireless sniffers with automated authorization.
10 of 10Example strategy
Construction company
The first steps toward cloud infrastructure have been taken, playing with test servers in Azure to see which applications can run in the cloud.
Today, the company still relies heavily on traditional infrastructure such as servers and central storage, and many mobile devices such as tablets and smartphones are used on its construction sites. Printing still plays a very important role, as security goes beyond hardware and software for a construction company. Many construction companies are victims of CEO fraud or Whale Phishing: the human aspect should not be overlooked either.
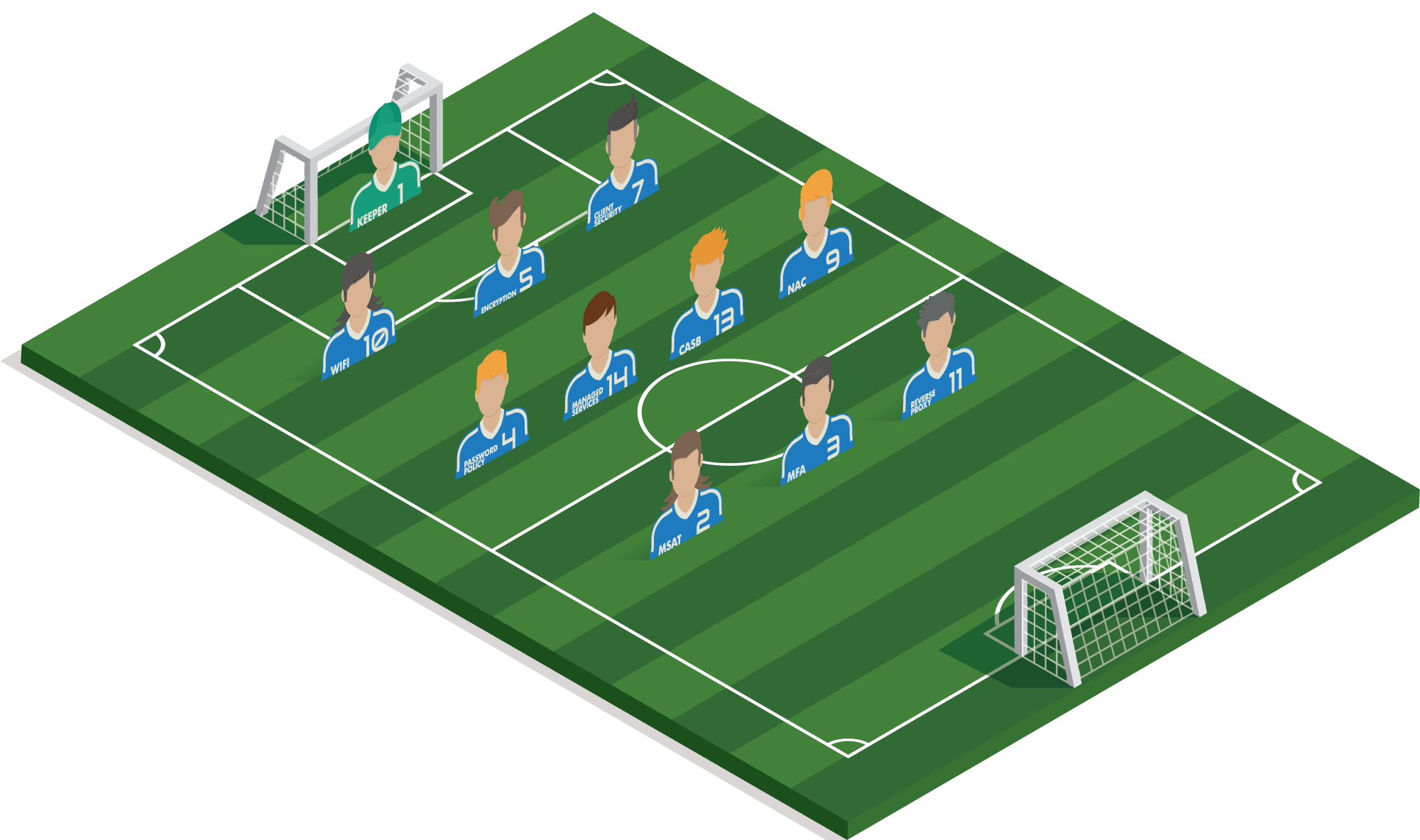
#1 Goalkeeper
A collection of essential interventions: antivirus, antispam, sandboxing, patch management, backup and firewall.
1 of 11#5 ENCRYPTION
Ensure that sensitive customer data is not on the street in the event of theft or loss. A laptop or tablet is quickly stolen!
2 of 11#14 MANAGED SERVICES
The uptime of the (web)shops is vital. Keeping all the infrastructure in all the shops up to date and under control is a huge challenge. Leave this to 24/7 experts so that your IT team can focus on strategy.
3 of 11#3 MFA
If an employee's login+password is still being misappropriated, criminals are powerless because they lack an extra code or biometric data.
4 of 11#7 CLIENT SECURITY
Quick and easy, but safe login with facial recognition and/or fingerprint is very useful. Moreover, you are extra assured of a safe working system.
5 of 11#4 PASSWORD POLICY
Employees who leave service can be quickly ‘excluded’ from applications. One breach will also not ensure that all systems can be hacked at the same time.
#2 MANAGED SECURITY AWARENESS TRAINING
E-Commerce is susceptible to phishing (lots of customer and credit card data…) it is important that all staff members handle sensitive data correctly.
7 of 11#10 WIFI SECURITY
Employees must be able to work safely and quickly, protected from the customers in the shops.
8 of 11#13 CLOUD ACCESS SECURITY BROKER
The amount of layers of security depends on location, amount of rights, the device used… To prevent unauthorized access.
9 of 11#11 REVERSE PROXY
A webshop full of personal and payment data requires maximum security. You also want to avoid downtime, so the protection against DDOS attacks, among other things, is an added bonus.
10 of 11#9 NETWORK ACCESS CONTROL
Secure physical access to the network so that customers cannot connect their devices to the company network either on the protected Wi-Fi (even with a password) or by cable.
11 of 11Example strategy
Retailer
A chain of clothing stores with several branches and a webshop. Customers and staff make continuous use of the available Wi-Fi, which also serves as an analysis tool to monitor the behaviour of shoppers. Each shop is equipped with interactive screens on which customers can order immediately. The webshop accounts for 33% of the business and is growing strongly.
They host their own webshop and work in Microsoft Dynamics 365 and Marketing for Dynamics 365 for their marketing automation.
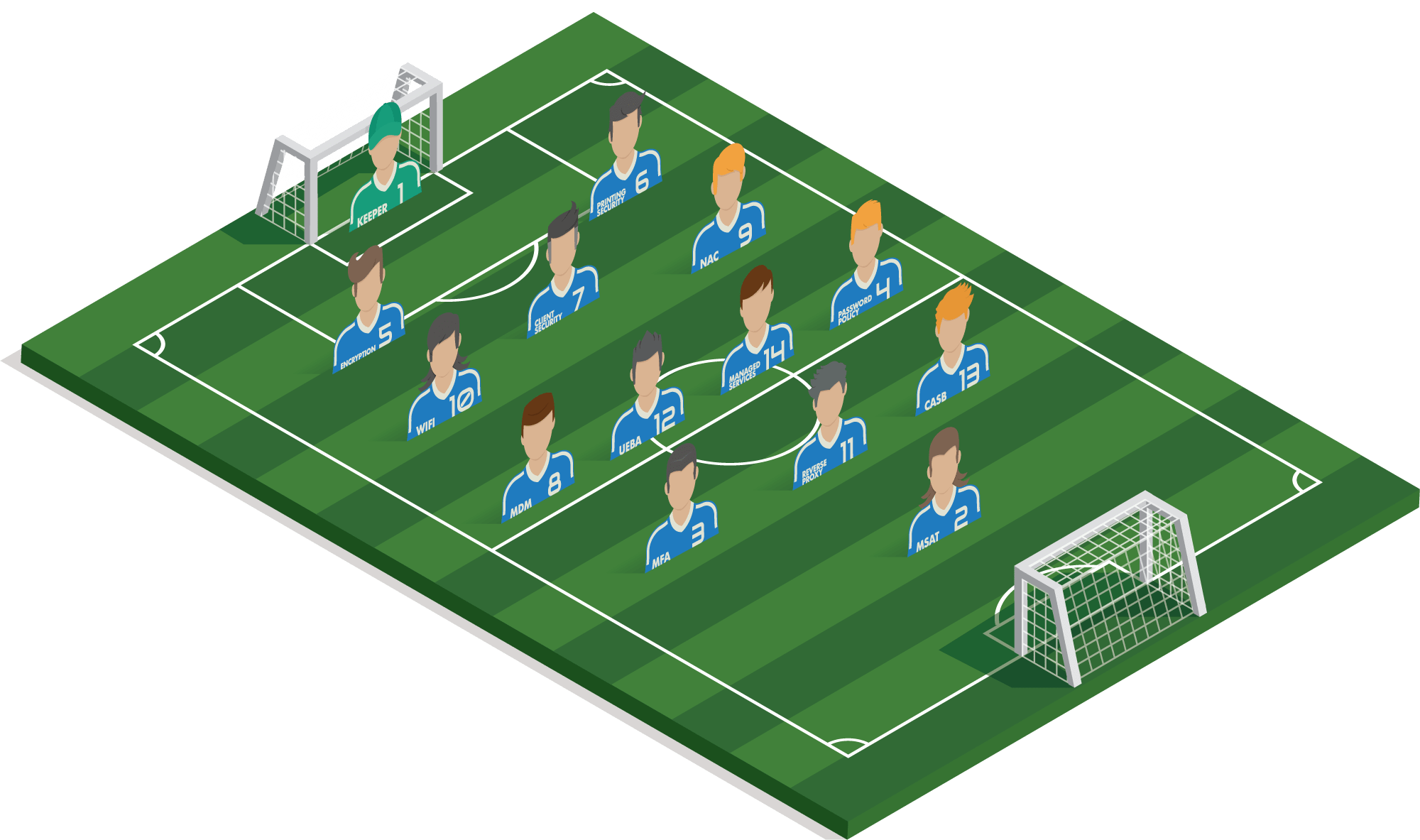
#1 Goalkeeper
A collection of essential interventions: antivirus, antispam, sandboxing, patch management, backup and firewall.
1 of 14#5 ENCRYPTION
Should PC’s or tablets still be on the street, third parties cannot access the (erased) data!
2 of 14#14 MANAGED SERVICES
Uptime is crucial and the environment is so complex that prevention and rapid detection & support in case of problems is essential.
3 of 14#3 MFA
A password is quickly extracted or even guessed. An extra code, fingerprint or verification on a nearby Bluetooth device can prevent valuable data from lying on the street.
4 of 14#7 CLIENT SECURITY
Ensure the integrity of your system by performing a BIOS check or by verifying software on a daily basis for suspicious behaviour.
5 of 14#4 PASSWORD POLICY
It may be ‘strong’, but using one password everywhere is insecure. How do you give colleagues one-time access, for example?
6 of 14#2 MANAGED SECURITY AWARENESS TRAINING
Large organizations always benefit from employees who can identify fake mails and sites.
7 of 14#10 WIFI SECURITY
Prevent outsiders from gaining access to the company's network.
8 of 14#13 CLOUD ACCESS SECURITY BROKER
An additional code is required if the employee attempts to log in from potentially insecure locations.
9 of 14#11 REVERSE PROXY
Your own domain is given extra protection because external parties do not have insight into your network.
10 of 14#9 NETWORK ACCESS CONTROL
Ensures that the roll-out of policies is applied in the same way at the different sites and that no unauthorised persons can enter the network.
11 of 14#6 PRINTING SECURITY
Prevents loose documents on devices and ensures that no one can read the print instructions/history
12 of 14#8 MOBILE DEVICE MANAGEMENT
A global organization requires easy management of all devices and access control
13 of 14#12 User/Entity Behavior Analytics
With A.I. and Machine learning, you can combat data theft thanks to real-time insights.
14 of 14Example strategy
Multinational manufacturing company
Multinational production company with HQ in Belgium and worldwide branches. The production runs 24/7, so it is vital that the production chain is never interrupted. Data is very important.
The company employs 1.000 people internationally. Visitors come and go and every day there may be other colleagues in the office. The internal communication is mainly done within Microsoft Teams and SharePoint.

#1 Goalkeeper
A collection of essential interventions: antivirus, antispam, sandboxing, patch management, backup and firewall.
1 of 14#5 ENCRYPTION
Should PC’s or tablets still be on the street, third parties cannot access the (erased) data!
2 of 14#14 MANAGED SERVICES
Keeping infrastructure and software up to date is impossible for our own team of application specialists and without forms of automation, that's why they best outsource it.
3 of 14#3 MFA
As an extra layer of security for the various cloud applications, an extra code must be entered in order to log in. For example, if a password is lost, there is no immediate risk of an infringement.
4 of 14#7 CLIENT SECURITY
Ensure the integrity of your system by performing a BIOS check or by verifying software on a daily basis for suspicious behaviour.
5 of 14#4 PASSWORD POLICY
With strong and unique passwords, you can also prevent a single breach from giving access to a large number of accounts.
6 of 14#2 MANAGED SECURITY AWARENESS TRAINING
Knowledge-based companies are often targeted to extract specific information. Staff must be continuously trained and kept alert in order to prevent this type of fraud.
7 of 14#10 WIFI SECURITY
Avoid SSID Spoofing or wireless sniffers with automated authorization.
8 of 14#13 CLOUD ACCESS SECURITY BROKER
An additional code is required if the employee attempts to log in from potentially insecure locations.
9 of 14#11 REVERSE PROXY
Your own domain is given extra protection because it is impossible for external parties to gain insight into your network.
10 of 14#9 NETWORK ACCESS CONTROL
Ensures that the roll-out of policies is applied in the same way at the different sites and that no unauthorised persons can enter the network.
11 of 14#6 PRINTING SECURITY
Prevents loose studies, research or blueprints on devices and ensures that no one can read the print instructions
12 of 14#8 MOBILE DEVICE MANAGEMENT
A knowledge organization requires easy management of all devices to enforce policies and provide access control. Stolen or lost devices can be immediately deleted.
13 of 14#12 User/Entity Behavior Analytics
Not only hackers, but also staff can get rid of valuable data/research. With A.I. and Machine learning, you can combat data theft thanks to real-time insights.
14 of 14Example strategy
IP BASED COMPANY
A research institute where employees must be able to work mobile and flexible within Office 365 to create and share information.
The company relies entirely on its Intellectual Property and the knowledge of its employees, who have their own data centre.
How are the players on your field?
Not all players are necessary in every situation. Others are.
In an open discussion with our specialists, you can indicate your requirements and challenges,
so we can work together to find the ideal position.
Put together the perfect strategy with our experts!
VAT no.
Daily Health Check
On the one hand we have a 24/4 (4h or 1h) SLA in our Managed Services but with the ‘daily health-check’-service, our certified experts will log on to your portals of the security solutions we support on a daily basis. They will check whether everything still works without problems and/or whether certain things need to be adjusted. You will receive a daily report and enjoy an extra safe environment!
- Whitepaper
- Webinar
- Webinar